Enterprises must realize that 100% cloud platform neutrality is more an illusion than reality, nor can it be enforced by barring all platform-specific services. Instead, this overshoots the mark, limits the benefits of the cloud, and overlooks the real multi-cloud challenges.
In the era of client/server computing, everyone laughed at the quote from Thomas Watson, chairman of IBM, who stated in 1943: “I think’s that there’s a world market for maybe five computers”. However, 80 years later, it looks like he was right after all. Basically, there are Amazon Web Services (AWS), Microsoft Azure and Google Cloud Platform (GCP) plus two cloud platforms in China. Even though Watson had probably five mainframe computers in mind, whereas the cloud platforms consist of an unimaginably large number of servers running in a multitude of data centers around the world, it is viewed abstractly the same.
Be aware that we are on the path where almost all IT applications of all Western world enterprises run on three hyperscale cloud platforms: AWS, Azure or GCP. Also note that while there are many software providers, their SaaS solutions are increasingly running on these platforms, too. From a political and competition law perspective, this may be worrisome, but from an individual company's viewpoint, cloud adoption is crucial to competitiveness and business agility; the benefits are huge. So, enterprises move to the cloud, but do not want to commit to a single platform; instead, pursue a multi-cloud strategy with two or even three platforms.
Compliance to regulatory obligation
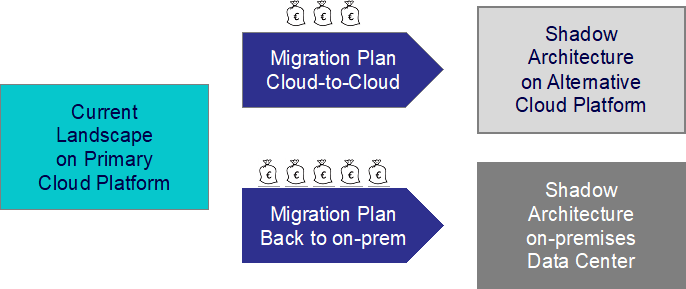
Particularly in the Financial Industry, a certain degree of platform neutrality is not just an architectural guardrail, but a regulatory obligation. For example, BaFin in Germany requires all insurers to have an exit strategy defined, i.e., insurers must be able to move their applications from current cloud platforms to others or back to on-premises. Note that this VAIT obligation does not require a 100% platform-neutral solution, but “only” a defined exit strategy and migration plan. This is often overinterpreted.
Frequently the illusion is created, and top management is led to believe that it is possible to move workloads between cloud platforms at the push of a button. This can be show-cased for small applications but is hardly feasible for the entire IT landscape. The fallacy often drawn is that you can move at will between the cloud platforms if you only use platform-independent services. However, the problem is not so much the services used, but data, virtual networks, security mechanisms and cloud operations.